SSH Tunneling
By Kalyani Rajalingham, published 22/06/2020 in Tutorials
In SSH tunneling, an encrypted channel is created between an ssh client and an ssh server. Information flowing within the encrypted tunnel is secure and thus cannot be intercepted. This type of service is in particular used when running insecure protocols such as TightVNC. They can also be used to access internal networks and services running on them, bypass firewalls, as VPNs and as backdoors.
To install ssh, open a terminal and type:
sudo apt-get install openssh-server openssh-clientOn Windows, although SSH Client is already installed, most people use PuTTY.
There are three types of SSH Tunneling: dynamic port forwarding, local port forwarding, and remote port forwarding.
Dynamic SSH Tunneling
In dynamic port forwarding, a SOCKS proxy server is created and connections established can access a vast number of ports.
ssh -D <local port> <server>Suppose that at work, they have blocked certain websites, and that you wish to peruse them. In this case, we can use dynamic SSH tunneling to bypass the blocks.
For example, in a terminal, Jim would type:
ssh -D 8181 jim@34.56.344.565Next we open mozilla firefox and set the proxy settings to localhost and 8181. Now when you surf the web, your system will generate a SOCKS proxy on port 8181 of Jim’s machine. These are great for accessing restricted sites.
Local Port Forwarding
Connections are forwarded from an SSH client to an SSH server and then to a destination server. In other words, the SSH client listening on a particular port tunnels it to a remote machine with the SSH server and further forwards it to a port on the destination server (which is either the SSH server machine or yet another machine).
ssh -L <local port>:<remote address>:<remote port> <server>For example:
ssh -L 9878:192.168.2.13:8080 34.56.344.565The client machine listens on port 9878, and when required forwards incoming traffic on said port to 192.168.2.13:8080. In other words, SSH binds to port 9878. Any traffic coming to port 9878 is forwarded through the encrypted channel to the SSH server (34.56.344.565) and then to port 8080 on 192.168.2.13 which is on the same internal network.
In another instance, suppose that the final destination were the server itself, the code would look something like this:
ssh -L 5901:localhost:5901 34.56.344.565Here, we wish to connect to the VNC server on the remote machine. The client machine is listening on 5901, and when a connection is established on 5901 via VNC viewer, it will tunnel the connection to the remote machine on localhost:5901 (of the server).
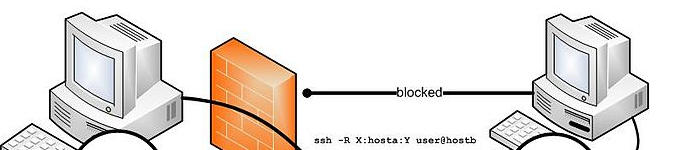
Remote Port Forwarding
A connection is forwarded from an SSH server to an SSH client and then to a destination server.
ssh -L <server port>:<client address>:<client port> <server>For example:
ssh -R 9878:192.168.2.13:8080 34.56.344.565Here, the server listens on port 9878 and tunnels all traffic on that port to 192.168.2.13:8080. Here, the final destination is 192.168.2.13 and the server’s ip address is 34.56.344.565. All traffic is tunneled to port 8080.
ssh -R 8080:localhost:80 34.56.344.565In this case, the server’s address is 34.56.344.565, and is listening on port 8080 (on the server). Here, we forward port 8080 to localhost on port 80. The final destination is the client itself.
SSH tunneling is a great tool to use when we need an encrypted connection. It has a wide set of uses that allows it to be abused by hackers.