The Complicated Firewall
By Kalyani Rajalingham, published 07/05/2020 in Tutorials
Until recently, I was content using the Uncomplicated Firewall that comes built-into Ubuntu. And it's called uncomplicated for a reason: its complicated counterpart – the iptables. It's not to say that iptables are difficult to comprehend or even impossible to use, but is rather massive. In other words, it has immense capacity and functionality, and as such is perhaps a lot more complicated.
Iptables are used for ipv4 packet filtering as well as NAT. For ipv6, there's ip6tables. Iptables allows its users to configure incoming/outgoing traffic to be modified, allowed, denied or re-routed. An incoming packet is passed through the table rules one by one. If it matches an existing rules, the action is carried out. If it does not, by default, it is allowed in.
Details of Iptables can be viewed via command line. Open an type in a terminal:
iptables –helpHowever, this section does not hold its immense capacity. In fact, almost 99% of its functionality is not described in the help section, but rather found in obscure documents.
But iptables aren't as crazy as they sound, they can be subdivided into three sections: tables, chains, and targets. Almost all of which is not in the help section.
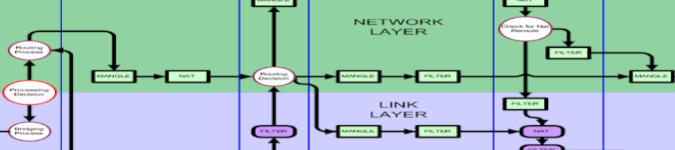
Tables
iptables –table <mangle|raw|security|filter|nat> rulesThere are 5 tables in iptables: mangle, filter, nat, raw, and security. The default table is the filter table (where –table isn't specified). The filter table, as its name suggests, is used for filtering incoming traffic. The mangle table is used for packet header alteration. The nat table is used to re-route packets by altering the source/destination addresses. That's not to mention the remaining two tables that seem to used much less frequently.
Chains
iptables -t <table> -<A|C|D|I|L|S|F|Z|N>
<INPUT|OUTPUT|FORWARD|PRE-ROUTING|POST-ROUTING> rulesThere are 5 chains in iptables: input, output, forward, pre-routing, and post-routing. However, not all tables can access all chains. For instance, there are three chains associated with the filter table: input, output and forward.
|
Pre-routing |
Input |
Forward |
Output |
Post-routing |
Raw |
Yes |
|
|
Yes |
|
Mangle |
Yes |
Yes |
Yes |
Yes |
Yes |
Nat (DNAT) |
Yes |
|
|
Yes |
|
Nat (SNAT) |
|
Yes |
|
|
Yes |
Filter |
|
Yes |
Yes |
Yes |
|
Security |
|
Yes |
Yes |
Yes |
|
Targets
Targets in iptables are configured to deal with a packet if they match a rule. The most widely used modules are Accept, Drop, Queue and Return. However, the following are available target modules: accept, balance, classify, clusterip, connmark, dnat, dscp, ecn, ipmark, ipv4optsstrip, log, mark, masquerade, mirror, netmap, nfqueue, notrack, redirect, reject, drop, same, set, snat, tarpit, tcpmss, tos, trace, ttl, ulog, and xor. For instance, the target DNAT rewrites the destination ip address of the packet.
There are so many target that I couldn't count them all. Some targets can only be used with some tables or chains, and using the wrong chain or table will throw an error. Perhaps this is why they call it the complicated firewall, it definitely requires that the manual be read from page to page before being able to use it.
For example:
1) In the filter table (by default), let's append a new rule to the input chain:
iptables -A INPUT -s <address> -j <ACCEPT| DROP| QUEUE| RETURN>For instance, to allow ssh on port 22:
iptables -A INPUT -p tcp –destination-port 22 -i wlan0 -j ACCEPT2) Changing the source ip address of a packet is done with the NAT table and the target SNAT (the target module that modifies the source ip) as follows:
iptables -t nat -A POSTROUTING -p tcp -o <interface> -j SNAT –to-source <ip>3) Changing the destination ip address of a packet is done with tge NAT table and the target DNAT (the target module that modifies the destination ip) as follows:
iptables -t nat -A PREROUTING -d <ip> -o <interface> -j DNAT --to <new ip>4) Change the time to live of an incoming packet is carried out with the Mangle table and the target TTL:
iptables -t mangle -A PREROUTING -i <interface> -j TTL --ttl-set <value>5) Port Forwarding
iptables -t nat -A PREROUTING -i <interface> -p tcp –dport <port> -j DNAT –to-destination <ip>
iptables -A FORWARD -i <> -p tcp –dport <port> -d <destination ip> -j ACCEPTOne must note that if a packet doesn't match any of the rules, then the default policy (ACCEPT) is applied. Iptables is a lot more complex with many many alternatives to carry out almost anything.
This is the beginning of iptables. The program itself is capable of so much more that it is the reason why we call it the complicated firewall. UFW (the uncomplicated firewall) has at most 5 variables.