Rainbow Tables
By Kalyani Rajalingham, published 16/06/2020 in Tutorials
All passwords in all databases are stored as hashes. Even on a Windows machine, when you set your password, the system doesn’t store the password in plain text – it doesn’t keep it in a readable format. It is instead passed through a hashing algorithm that turns the plain text password into a hash. The hash is then stored. Whenever you type your password again, it is once again passed through the hashing algorithm and compared with the hash in the database, if the two match, you are given access. The problem however is that hashes cannot be reversed.
Plaintext → hashing algorithm → hash
password → NTLM hashing algorithm → 4F2DBC410D627862C8A0E7DCC7A41978
In this case, the word password is stored as 4F2DBC410D627862C8A0E7DCC7A41978 on your Windows machine.
Now, when you get a hold of a computer too, what you will retrieve is the hash, not the plain text password. In other words, let’s say you find a computer in a bar, and bring it home. When you open it up, you can retrieve all the passwords stored in the hashed format. That means that the owner’s Facebook password is stored as an NTLM hash. Which brings us to the next problem: how do we reverse hashes?
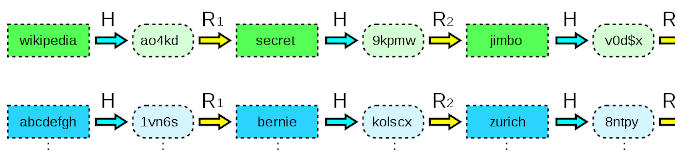
Hashes are irreversible, and as such there is no way to go back from the hash to the plain text word, however, we can attempt comparisons. What we can do instead is to take a random set of words or a word list, and turn them into hashes and compare the hash we have to the generated hash. This is where the rainbow tables come in.
Rainbow tables are a pre-computed set of hashes along with their plain text words. It’s kind of like a dictionary with all possible passwords and their corresponding hashes. During a bruteforce attack, a word in a wordlist is first hashed and then compared to a target hash. The advantage of using a rainbow table is that it allows us to skip the first step – there is no need to hash the wordlist, it is already in a hashed format, and as such we simply compare the target hash to those in the hash database. However, rainbow tables are large and thus require vast space for storage (27 - 864GB).
Install RainbowCrack
To install rainbow tables:
(I) first and foremost download RainbowCrack from https://project-rainbowcrack.com.
(ii) Extract it
tar zxvf <rainbowcrack-1.7-linux64.zip >(iii) Enter the new directory
cd <extracted directory>(iv) configure
./configure(v) compile
make && make installNow, let’s generate the rainbow tables.
Generate Rainbow tables
To generate the rainbow table, open a terminal and type:
rtgen hash_algorithm charset plaintext_len_min plaintext_len_max table_index chain_len chain_num part_indexFor example:
rtgen md5 loweralpha-numeric 1 8 0 3000 4000 0- hash_algorithm: the hashing algorithm such as MD5 or NTLM.
- charset: character set to use
- plaintext_len_min/max: length range
- table_index: for reduction function
- chain_len: chain length
- chain_num: number of chains to generate
It takes a few hours to generate the tables. The generated files have an extension of .rt. If we wish, we can also purchase the precomputed tables.
To sort the rainbow tables generated, type:
rtsort <rt file>While sorting, we cannot interrupt the program.
Crack a hash
To crack a single hash, type:
rcrack <location of rt file> -h <hash>To crack multiple hashes, type:
rcrack <location of rt file> -l <hash file>Happy Cracking!
[Editor's Note/Disclaimer: Information in the above article was for education and ethical hacking practices]